Vegetation Management
Beyond The Border Zone
April 25, 2024
Wildfire
Utility Investment In Forest Restoration
April 18, 2024
Smart Grid
Reimagining The Future Grid
April 17, 2024
Sponsored Content
Sponsored Content
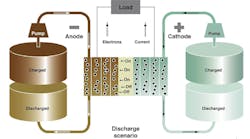
Renewables
Battery Energy Storage Systems | QuickChat
April 18, 2024
Renewables
Aerial Spacer Cable in Renewables Applications
March 27, 2024
Sponsored Content
Jobs
Jobs